Advanced Threat Protection
in the Cloud
The need for advanced threat protection that inspects the growing about of encrypted traffic is a must for all organizations concerned with having robust cybersecurity. Using the cloud is a perfect way to address this need allowing advanced anti-virus and AI tools with scalability to achieve best in class protection.
THE CHALLENGE
It’s a steadily increasing problem for security everywhere, every day. Encrypted traffic—using HTTPS tunneling protocols via webpages or other sites—is becoming a trojan horse for cybersecurity solutions like firewalls that try to inspect this encrypted traffic, traffic that we now know is in fact starting to smuggle malware into networks. In fact, leading analysts estimate more than half of the network attacks targeting enterprises used encrypted traffic to bypass security controls. But enabling SSL inspection on a traditional firewall is not the answer: testing agencies show that the throughput of the device drops with 60-80% as its CPU is strained to decrypt and re-encrypt traffic plummets. This means that either multiple expensive hardware appliances must be utilized or a dedicated appliance needs to be deployed.

Advanced Threat Protection – complementary to any firewall
On prem or in the cloud, you choose. Find out which Clavister NetEye product is best to protect your business.
DOWNLOAD DATASHEETHOW TO SOLVE IT
Luckily, there’s a better way to attain SSL inspection and compliance concerns that delivers a fast, scalable and excellent TCO. It’s called Clavister NetEye Cloud and it uses the power of the cloud—the best place to do such high-volume computing—to deliver the fastest and most affordable full de-coding and filtering of encrypted web traffic available. Clavister’s NetEye Cloud is our powerful private cloud that has a powerful SSL inspection engine built in, with the added muscle of the fastest anti-virus signature updating in the market to deliver up to the minute malware detection as it burrows into the traffic at cloud speeds. Protect, log and report on SSL web activity at enterprise speeds. No client software required.
On top of that, it uses a powerful predictive AI engine that gives additional cybersecurity protection. Last but not least, using our Clavister NetEye Cloud Sandbox product, malicious .exe files are sent to a secure private instance where they’ll be detonated and observed providing reports back to the security administrator for further action. With an Advanced Threat Protection Cloud Servicee run complementary to the firewall, dedicated resources are focused on scanning content holistically and efficiently – with multiple scanning engines.
This setup not only secures all traffic proxied through the main HQ firewall, it also scans traffic coming in from branch offices and remote workers via VPN. In an ideal setup the VPN client on the remote computers are setup to always connect and proxy all traffic. This allows the Advanced Threat Protection product to protect the whole office – on-site, at remote sites and even the workers on the road.
With Clavister NetEye Cloud, you’ll be able to trust the traffic that’s coming through your network because you’ll now know what’s in it… and you’ll be able to do something about it.
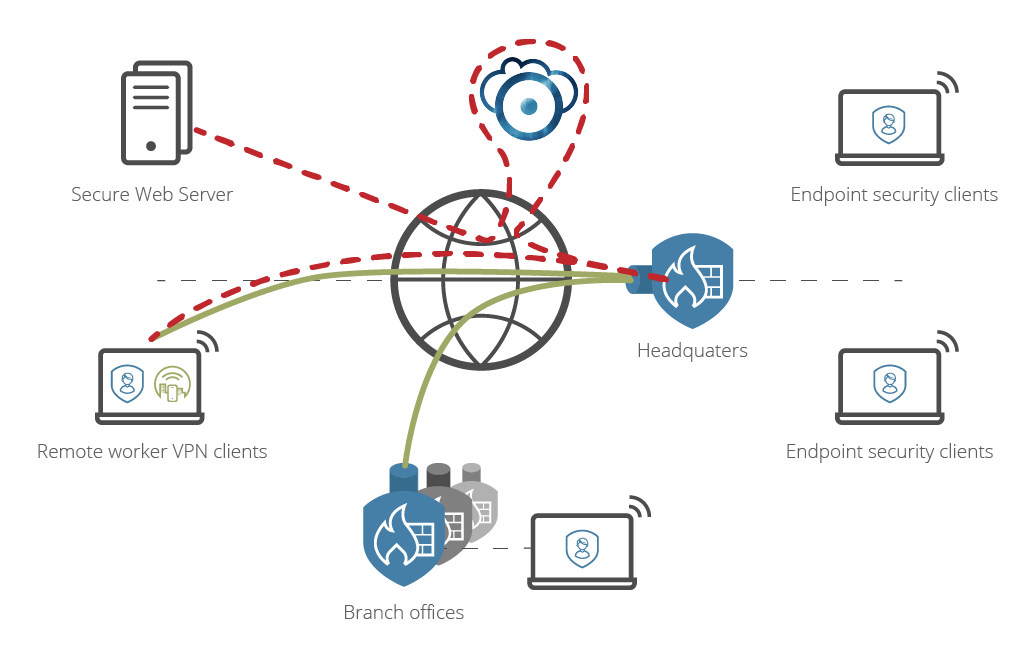
With Clavister NetEye Cloud, you’ll be able to trust the traffic that’s coming through your network because you’ll now know what’s in it… and you’ll be able to do something about it.
Clavister NetEye Cloud Services
Our Advanced Threat Protection Cloud services are designed to complement any perimeter security solution. Clavister also offers virtual and hardware appliances for on premises threat inspection.
Use Cases for the NetEye Firewall
Use cases are the way our Advanced Threat Protection product solves your problems. Read a few here to see how we do it.

ANTIVIRUS / MALWARE SCAN
Streaming scanning of attachments in mail, web and files for malicious content
READ MORE
ENCRYPTED TRAFFIC INSPECTION
Server traffic decryption for full inspection of inbound traffic
READ MORESolutions
Explore some of the solutions that we have provided which are supported by Clavister Advanced Threat Protection products and services.
SOLUTION
Protected (Remote) Office
Protect the connections from
other operators
SOLUTION
Internet Content Control
Protect business critical systems within the core network












